The threat of hacked passwords or a data breach are nightmares as a business owner.
It will keep you up at night.
It is essential to know precisely what is data integrity is to ensure your business is safe at all times.
Understanding how to provide data security can help your business stay protected, or you may end up with costly data recovery solutions.
What Is Data Integrity?
Data integrity refers to the accuracy of data.
Integrity is vital to your success and reputation. Keep in mind the term can refer to many things. The two main ones are a state or process.
You will also sometime hear the reference”data quality.” That can lead to some confusion.
What Ensures Data?
For data to have “integrity,” it must have a complete or whole structure.
This means that every quality of the data must conform to a standard model. That ensures nothing gets compromised and remains accurate.
Remember, you do have options. You want to ensure your the accuracy of your information.
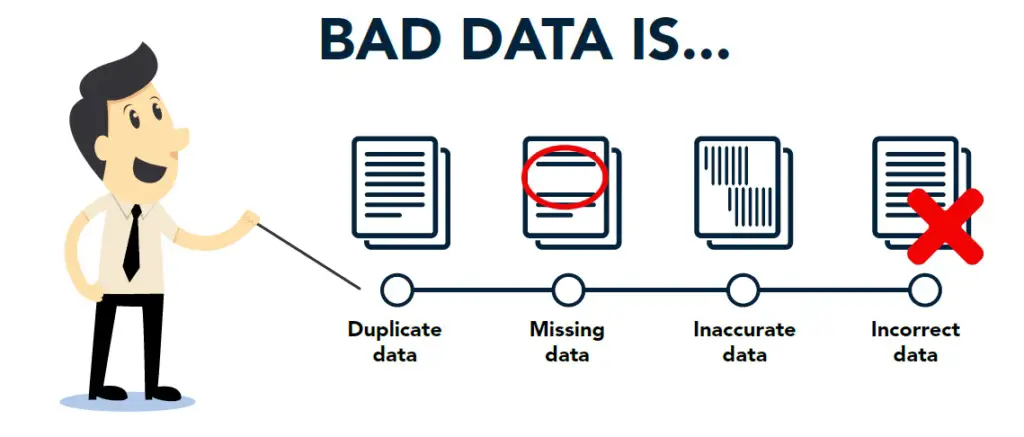
Data Integrity Examples
Integrity examples include anything that involves information stored in databases and servers.
A well-known example involves customer information. These are credit card details and addresses. Online merchant store these on a server.
Other notable types include medical records in healthcare offices. They also include files in ph*rmac*utic*l companies.
Many instances of integrity restraint can be in SQL servers. An SQL server is Microsoft’s relational database management system is also on SQL servers. An SQL server is Microsoft’s relational database management system.
Why ensuring data is Important
Data integrity is vital to its security online. The process ensures files can be retrieved. They provide connections.
They can increase stability and performance and drives decision-making. If you consider the information integrity of your business, be aware that compromises can occur. Examples include:
- Human mistakes
- Errors when transferring data
- Cyber threats in the form of viruses, malware, and other hackers
- Hardware failure
- Damage to physical devices
Keeping data secure can be vital. You need to have the right protection in place.
How To Test Information Integrity and security
Data’s integrity gets tested if a default value can be retrieved. Validation also ensures every value gets saved in a database. Data compatibility must get checked against older hardware and operating systems.
Data must get verified to change it in tables. By running these tests, integrity remains up to date and accurate.
How To Improve Data Integrity
There’s a variety of ways to improve types of integrity. While the options can be creative and quite technical, the processes are simple to grasp. A few ways to prevent data loss include using a single source for the information. Consider these three methods as well.
- Use Assessments To Identify Potential Gaps
- Use of services can help prevent human error
- Plan Ahead
A company’s database management system should improve processes for data. Companies should not wait for a regulatory inspection to get their data quality measures up to par.
Keep In Mind Other Implications
The information that has no protection can lead to loss of customers.
You do not want to lose the trust of your brand. That is why we ensure a positive approach that keeps this focus. Don’t forget who your clients are and why their data protect is so essential.
Knowing how to improve your data security is a good move when going forward with your online business.
Data integrity is not just about protection of digital information. Keep in mind that for every bad data out there, there is a consequence to your business. That is why we have compiled this list of seven critical facts.
Knowing them will allow you to see just how vital it is to keep customers information safe. Keep in mind that as you read, you will want to take notes.
Many Companies Now Demand Examination of a company’s database management system.
An article in Business.com states many companies demand to test a company’s level of integrity. They are using policies to ensure regular examination. That includes reports detailing disparities in data. These procedures are often put in place to prevent more significant issues with data integrity.
These types of key values Is Important in Decision Making
Decisions based on security programs is growing.
It moves in volume at a rate of 40 percent a year. That information comes from a 2014 PwC survey. The importance of accuracy and complete information integrity will become even more vital.
Bad Data Integrity Results in Failed Business Goals
Gartner states 40 percent of businesses will fail to achieve their business objectives. That is due to poor data quality. That means an increased demand for protection of customers information. You must ensure your company’s success.
Bad Data Security Can Lead to a Decrease in Employee Performance
Again, Gartner states there was a 20% decrease in employee performance. That was a result of weak security programs. That can lead to low performance. Worse, it is a waste of time effort.
It Poses Significant Challenges to Healthcare Providers
Many providers of healthcare also face significant challenges.
There is a vital need for coherent records and to maintain unified files. Weak integrity checking can result in dire consequences. These range from HIPAA data security violations to inadequate patient care.
As a result, the US FDA has issued guidelines to ensure proper protocols. They state that data should be reliable and accurate. Companies should use effective strategies to manage integrity security risks. They also define common integrity terms.
They address the exclusion of CGMP data, ensure workflow validation, data access, audits, electronic records, and personnel training. The FDA spells out testing requirements and ways to improve data integrity. With these guidelines, companies face significant challenges.
Poor Data Integrity Can Be Costly
Poor entity integrity can lead to many headaches. They can even cost your business in the long run. Three types of damages that can occur are:
- Data may be unrecoverable
- Lost data may need considerable time to restore
- Applications not related to lost data may fail
Data security is not only a problem for IT gurus. The potential costs to a company’s success are hard to ignore. Take a look at how much time and effort gets invested. That is an issue no one wants to deal with in the long run.
Final Verdict
Poor security programs can be detrimental to a company’s success.
Integrate states that primary key restraint usage will continue to rise. That will provide a significant obstacle for companies going forward. That is why we recommend that every business ensure their security program is up to standard.
