We all know how antivirus programs are essential for our online privacy and protection today. But how do they actually work?
Of course, you would know that an antivirus program scans, disables, and eliminates malware on your computer. But do you know how scanning takes place against so many different kinds of malware?
To understand the scanning process, we must also learn how different malware types spread so we can understand the various techniques antivirus programs use to detect and fix those attacks.
That’s why we’ll try and explain both concepts side by side.
How Malware spreads and How Antivirus stops it?
Malware and viruses are software coding, of course, and they act as any other software program does. But what makes them different is the objective they were created.
Malware is meant to attack, harm, or lock your computer. It can steal your information, encrypt or erase important data from your computer, turn local apps into spyware or your device into a bot, and much more.
Using Data Mining to Identify Malware Types
Since each malware type has a different function, they each have different routes to enter your system and affect different components. Each one has its own signature that makes it recognizable for antivirus programs from other apps.
Antivirus programs are backed by huge databases that contain definition files of all the known malware types. These databases are continuously updated as new types are found.
That’s why the antivirus first scans its own database for matches when it comes across suspicious coding. Once a match is found, the antivirus will automatically delete or isolate the corrupt file or app.
This type of scanning is called Specific Detection. However, a more Generic Detection approach also exists, which even considers the variants of malware families.
Since many malware types use modified signatures of old samples, this technique is also effective. In this approach, the antivirus program also isolates an app based on a common codebase with known malware types.
Detecting the Behavior of an Executable File
However, what about new malware threats? How do antivirus programs identify malware types that are unknown to them?
Look, hackers are fully aware of how antivirus programs work. They know how an antivirus software will search and examine each and every combination of 1’s and 0’s until it makes sure your system is completely malware-free.
That’s why hackers use their own tricks to disguise malware as legitimate apps. One way hackers do that is by using encryption. Antivirus programs also use this technique but to protect your information and make it inaccessible.
But hackers use encryption to disguise malware programs or part of their signatures so that they can’t be matched to virus definitions.
What encryption does is that it locks up sensitive data under an impassable lock. Depending on what level of encryption has been used, it might become virtually impossible for antivirus software to decipher or decrypt the contents of a file.
As a result, the antivirus is unable to even detect the malicious file, let alone block it as a threat. Malware sometimes also hides inside safe software.
A trojan is an example of such software that disguises itself as a safe software code. Trojans can hide inside other apps such as games and even software patches. They may also be planted into the attachments with phishing emails.
Another technique used by modern hackers is self-mutilation. Using this technique, malware will first infect your device and then further create new versions employing more complex obfuscation techniques.
Hackers create these viruses on the pattern of complex biological viruses. The objective is to make their detection harder by antivirus programs.
The mutation is the most advanced technique used by hackers. This form of the virus is also called a Metamorphic Virus. The MSIL/Gastropod virus and Zmist are examples of metamorphic engines.
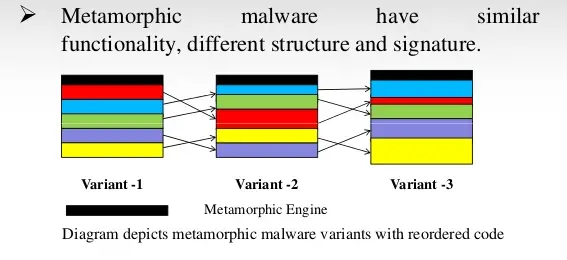
Similarly, polymorphic malware types have the ability to change their code to avoid detection. According to the Webroot Threat Report, 93% of all malware types observed in 2018 were polymorphic.
This type of malware infection doesn’t only make detection much harder but also wreaks havoc on your system. If before, your antivirus program was putting out small fires here and there, now it is up against a full-fledged wildland fire.
But worry not, antivirus programs also come with tricks of their own. And that’s why they use Heuristics to identify and block new or complex malware threats. This approach uses data mining as well as machine learning techniques to monitor and learn the behavior of an executable file.
For instance, if your antivirus software sees that an app is trying to interact with every .exe or executable file on your computer, the antivirus program labels it as a new, unknown malware type.
However, this method does end up flagging some legitimate software as malware as well. Nevertheless, this is an effective detection approach that helps to block unknown malware attacks.
How does Real-time Scanning work?
Beyond these detection techniques, antivirus programs also use different scanning methods to provide thorough protection against malware threats.
These days, you often hear about real-time monitoring, which is a type of constant scanning by antivirus programs.
While you carry on with your daily work routine, your antivirus software is continually running in the background, checking every file you open, every link you click on, and every website you load.
Also known as on-access scanning, resident scanning, or background scanning, this method is always scanning files, every time you open them.
To you, a file may seem to open immediately, but the antivirus has already checked it for malicious coding before it even opens.
This technique is fast, efficient, non-intrusive, and always on guard. Real-time scanning is particularly effective against malware types that constantly seek security holes.
For instance, worms seek out vulnerabilities in an operating system to install themselves. That’s why, although you can turn off this feature, it’s not recommended to do so.
Besides, when malware has entered your system, it’s much harder to remove it or to make a hundred percent sure that the malware has been removed after a full system scan.
Talking of which, let’s see why full system scans are important when there’s already constant scanning available.
So, why do we need Full System Scans?
Full system scans have their own purposes despite constant scanning. Let us explain to you why.
It is absolutely necessary to run a full system scan as soon as you download and install your antivirus program. The software will thoroughly rack your system for all kinds of malware and proceed to quarantine or delete them.
If it finds any suspicious coding, the antivirus will immediately block it or notify you if it needs your permission to go ahead with a particular fix. That way, your system is first cleaned off of all evil, and then the software can stand guard at all the entrances to your system.
Most antivirus programs schedule full-time scans at least once a week. This is so your software can examine your system against the latest virus definitions and scan for dormant malware types.
Remember, though; full system scans are only carried out when your computer is turned on and plugged into a power source.
Full system scans are also a good idea in many other situations. For instance:
- If you’re trying to repair an already infected computer
- If you’ve been using your device on public Wi-Fi
- If you’ve inserted your hard drive into another system
- If you’ve used multiple external storage drives to copy or transfer content
So, what about False Positives?
Because of the aggressive nature of heuristics approach and because of a huge number of software out there, antivirus programs can at times label a perfectly safe file as malware. This is called a false positive or false alarm.
Premium antivirus software like Bitdefender, Kaspersky, and Norton return very few false positives, as evident from the recent independent evaluations by the AV-Comparatives, which runs a test for false alarms as part of its Real-World Protection Test as well as a separate False Alarm Test.
However, in the case of premium antivirus programs, false alarms are rare, but they are possible.
For instance, in 2017, Google Play Protect flagged and removed a Bluetooth app from the Motorola Moto G4 mobile phone. This false-positive later resulted in users being unable to use Bluetooth at all.
Generally, though, you should believe when an antivirus tells you a file or an app is malicious. But if you’re not sure, you can try uploading the file to VirusTotal, a website owned by Google.
VirusTotal will scan your file using a variety of antivirus programs and let you know if each one identifies the file as a virus or not. If the majority of the programs say it’s a virus, you can give your antivirus program the go-ahead to remove the file from the system.
Does that mean you can trust all kinds of Antivirus Programs?
The simple answer is, of course, not. You can’t trust every antivirus for your complete protection. In fact, many free-of-cost antivirus software that seems perfectly legit may actually be harmful, especially if they come without a proven track record.
That’s exactly what WinFixer is. It’s a Windows-specific malicious software that disguises itself as a legitimate diagnostic tool meant to repair corrupt files and enhance system performance.
An unassuming user can easily fall victim to this malware just because of the name. The catch is in how it works, though. When you visit a website that has already been infected with this malware, WinFixer automatically installs itself on your computer.
Next, a pop-up window appears on the screen, informing you that your device has been infected with malware and offers a free scan. After that, it’s just a matter of clicking anywhere on the pop-up window, even the cross sign to close it, and the software will install itself.
Once the software is on your system, it starts sending frequent pop-up messages to your screen, claiming your PC has multiple malware issues. It then encourages you to purchase the upgraded version of WinFixer to fix your computer.
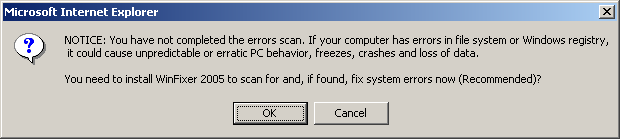
Additionally, WinFixer also installs itself into your device’s registry and then recreates itself every time you boot up your system.
This is just one of the countless examples where seemingly secure software turns out to be a big can of worms. That’s why you should always be wary of installing unknown software, freeware in particular.
It always costs you much more to fix your infected computer later on than to pay for good premium software.
Another problem occurs when you do have antivirus, but many types of malware still manage to slip through. This happens because of low detection rates. Again, it’s more common with lesser-known, cheap solutions.
That’s why you should always go for well-known antivirus programs. AV-Comparatives runs regular tests for antivirus detection rates. If you want to know what antivirus programs have high detection rates, you can find an answer with these detection rate studies.
It might also be helpful to compare the detection rates with the results of False Alarm tests. That way, you’ll know how legit those high detection rates are.
So, what do we learn?
Malware is becoming ever more complex. It can hide, adapt, disguise itself, and even rewrite or recreate itself. Put simply, your privacy and security are at much greater risk with every passing day.
That’s why top-ranking antivirus programs use a multi-pronged approach to detect and block malware threats of all types at various levels.
There are several excellent antivirus software available for Windows 10 these days. After all, prevention is the best form of defense, and it only comes with robust antivirus protection.
